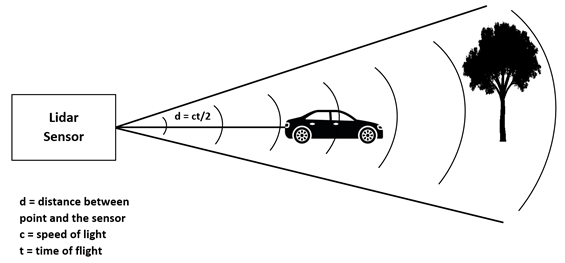
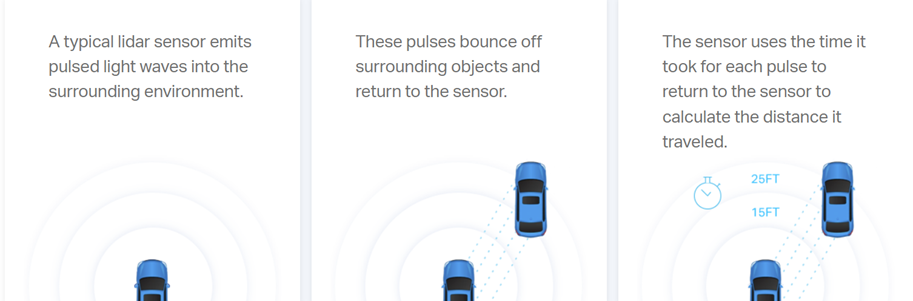
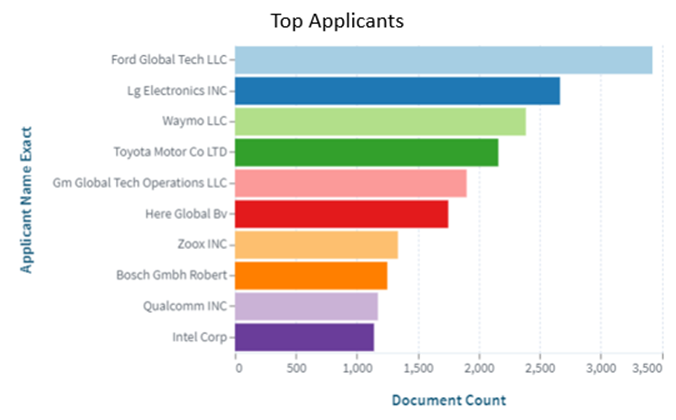
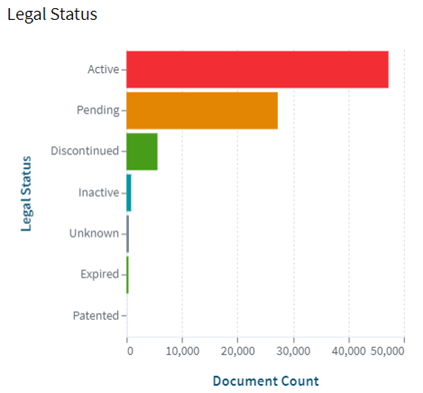
Introduction: The Impact of NLP and Conversational AI on Modern Technology
Natural Language Processing (NLP) and Conversational AI have evolved from niche research areas to transformative forces across industries. NLP enables machines to understand, interpret, and generate human language, while Conversational AI, a subfield of NLP, empowers systems to interact with people in ways that feel intuitive and human-like. These technologies are behind virtual assistants like Siri and Alexa, customer service chatbots, and even translation apps.
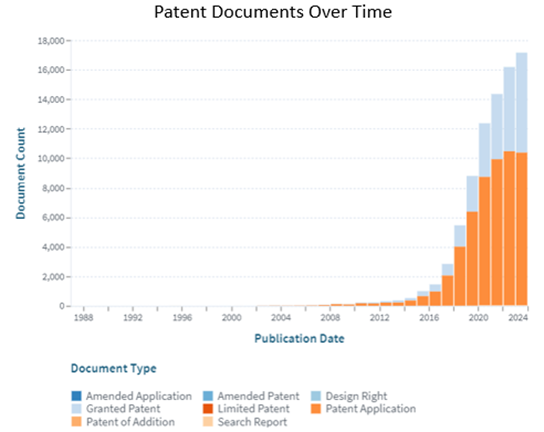
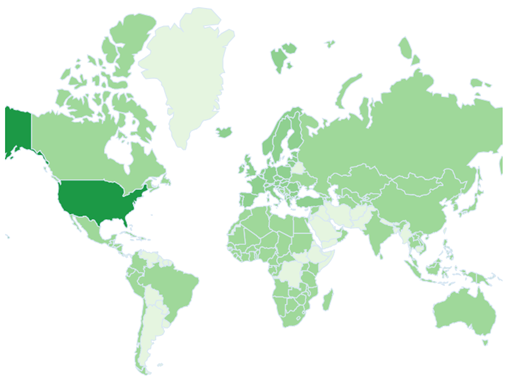
With this rise in application, the patent landscape for NLP and conversational AI has seen significant growth. Organizations are racing to secure intellectual property (IP) for innovations that span from core algorithms to advanced systems designed for specific use cases like healthcare, finance, and smart devices. In this post, we’ll explore foundational NLP techniques, the major components of Conversational AI, the role of patents, and emerging trends in this dynamic field.
Foundations of NLP: Core Components and Techniques
1. Text Preprocessing Techniques
NLP begins with converting raw text data into structured forms suitable for machine learning models, a process known as preprocessing. This stage involves several steps:
- Tokenization: Splitting text into smaller units, or “tokens,” like words or sentences.
- Lemmatization and Stemming: Reducing words to their root forms, which helps generalize the data.
- Stop-word Removal: Eliminating common words like “the,” “is,” or “and,” which typically don’t add much meaning.
2. Machine Learning Models in NLP
NLP tasks rely heavily on machine learning models, which fall into two main categories: supervised and unsupervised learning.
- Supervised Learning: Involves labeled data where each text sample has a known outcome, such as classifying a customer review as positive or negative.
- Unsupervised Learning: Uses unlabeled data to identify hidden patterns, such as topic modeling to categorize research articles.
3. Advanced NLP Models: Transformers and Large Language Models (LLMs)
The advent of transformer models, like BERT (Bidirectional Encoder Representations from Transformers) and GPT (Generative Pre-trained Transformer), marked a breakthrough in NLP accuracy. Transformers use self-attention mechanisms to focus on relevant parts of input sequences, allowing them to generate contextually accurate responses.
Conversational AI: Components of Engaging, Interactive Systems
1. Types of Conversational AI Systems
Conversational AI systems can be broadly divided into rule-based systems and AI-driven systems:
- Rule-based Systems: Follow pre-set rules for each user input. These systems are straightforward but lack the adaptability of AI-driven models.
- AI-driven Systems: Use NLP to interpret user intent, enabling them to handle complex interactions. They are used in applications like customer support bots and virtual assistants.
2. Components of Conversational AI
Natural Language Understanding (NLU)
NLU identifies the user’s intent and extracts relevant information, known as entities, from their input. For example, in a sentence like “Book a flight to Paris next Tuesday,” NLU would recognize “flight,” “Paris,” and “next Tuesday” as key entities.
Natural Language Generation (NLG)
NLG enables the system to generate responses, making the conversation feel natural. The system uses grammar rules or machine learning models to convert structured data back into human language.
Speech Recognition and Synthesis
Speech recognition and synthesis transform spoken language into text and vice versa, a critical component for virtual assistants.

The Role of Patents in NLP and Conversational AI
1. Types of Patents in NLP and Conversational AI
Patents cover a range of innovations in NLP and Conversational AI. Here are a few primary categories:
- Core NLP Techniques: Algorithms for tokenization, named entity recognition, and sentiment analysis.
- Conversational AI Frameworks: Patent protections for multi-layered conversation flows, intent recognition systems, and dialog management strategies.
- Hardware Integration: Patents that focus on integrating NLP and conversational AI with specific devices, such as IoT devices or smart speakers.
2. Noteworthy NLP Patents and Holders
Leading companies like Google, Microsoft, and Amazon hold influential patents in NLP. For instance:
- Google’s BERT Model Patent: Covers innovative aspects of the transformer model architecture.
- Amazon’s Alexa Patents: Encompass a wide range of speech processing and conversational flow technologies.
3. Regional Patent Trends and Challenges
The U.S., China, and Japan are major hotspots for NLP and conversational AI patents, with each region presenting unique challenges around data privacy, patent eligibility, and regulatory standards.
Emerging Trends and Advanced Patent Areas in NLP and Conversational AI
1. Multilingual NLP
With globalization, multilingual NLP is gaining traction, allowing companies to create applications that work across languages and regions. Patents in this area cover universal language models and techniques for efficient language translation.
2. Emotion and Sentiment Analysis
Emotion analysis allows conversational AI to recognize user emotions, making interactions more empathetic. This is particularly useful in customer service and mental health applications, where an understanding of sentiment can greatly improve user experience.
3. Domain-Specific NLP Applications
NLP models tailored for specialized domains—like healthcare, law, and finance—are rapidly emerging. Patents in these areas protect domain-specific applications such as medical diagnostic tools or financial analysis systems.

Challenges in Patenting NLP and Conversational AI
1. Patent Eligibility and Scope
One of the challenges in NLP patenting is defining patentable boundaries. Patenting algorithms and conversational flows often faces scrutiny for being abstract ideas rather than tangible inventions.
2. Ethical Concerns and Bias
AI models can inherit biases from training data, which is a concern for patent holders and developers alike. Patents must address the risk of biased NLP systems, as these can lead to unintentional exclusion or misrepresentation.
Future Directions for NLP and Conversational AI Patents
1. Explainable AI and Transparency
Explainable AI is essential in sectors like healthcare, finance, and law, where decisions need to be interpretable. Patents are emerging for NLP models that include mechanisms for transparency in decision-making.
2. Real-Time Processing with Edge Computing
Real-time conversational AI, enabled by edge computing, is reducing latency and enhancing privacy by performing data processing on local devices rather than cloud servers.
Conclusion
The rise of NLP and conversational AI patents illustrates the importance of protecting IP in this rapidly evolving field. Innovations in multilingual NLP, emotion recognition, domain-specific applications, and explainable AI continue to shape the landscape. As conversational AI becomes increasingly integral to daily life, patent holders are poised to set the standards for future advancements in technology.